The inability to perform actions requiring administrator privileges is a big limitation of Windows Quick Assist remote desktop. This is especially true in a business environment where your users should never have administrator privileges. The reason for this is User Account Control (UAC) security policies. UAC allows users to sign in using a standard user account and run applications requiring administrator privileges by entering the credentials for the admin account. When a user tries to perform an action that requires administrative privileges, UAC triggers a consent prompt:
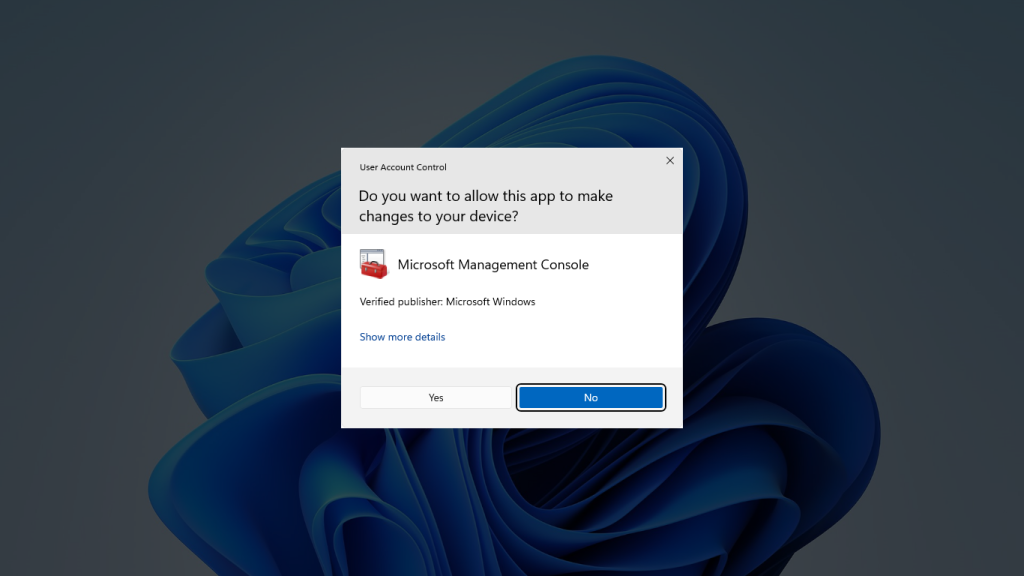
If you’ve ever used Quick Assist to perform a task that requires elevated privileges, then you know what happens next. When the pop-up appears either asking for consent or login credentials, all the remote user sees is a black screen. Quick Assist is waiting on the local user to enter the credentials or approve the consent prompt.
Here’s a workaround:
Open the command prompt and enter the following command:
runas /user:[username] cmd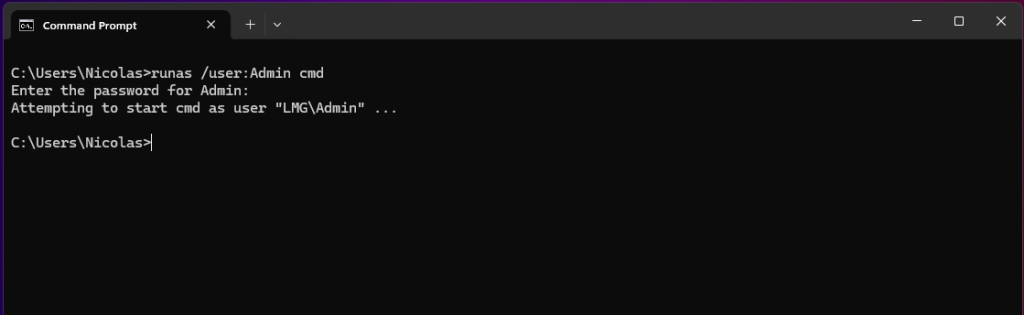
Replace [username] with the username of an account with administrator privileges and enter the password.
Now you will see a new command prompt, except now it is running with elevated privileges:
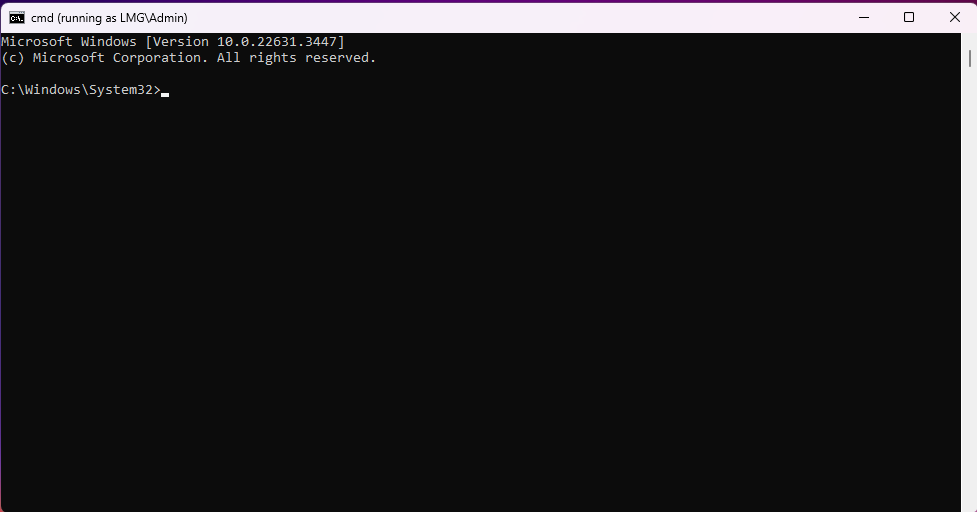
Now enter the following command (This will only work on Professional releases of Windows):
secpol.msc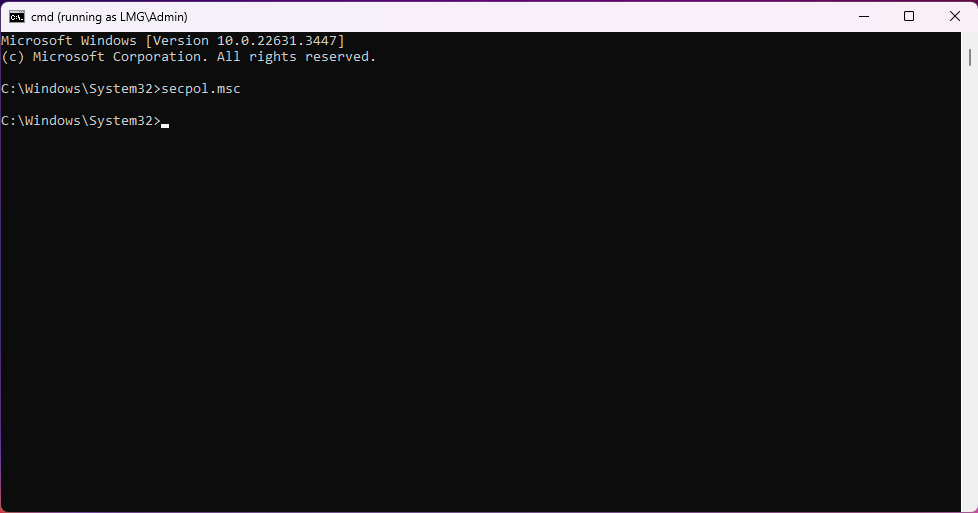
Now you will see your local security policies. Select Local Policies > Security Options > UAC: Switch to the secure desktop when prompting for elevation:
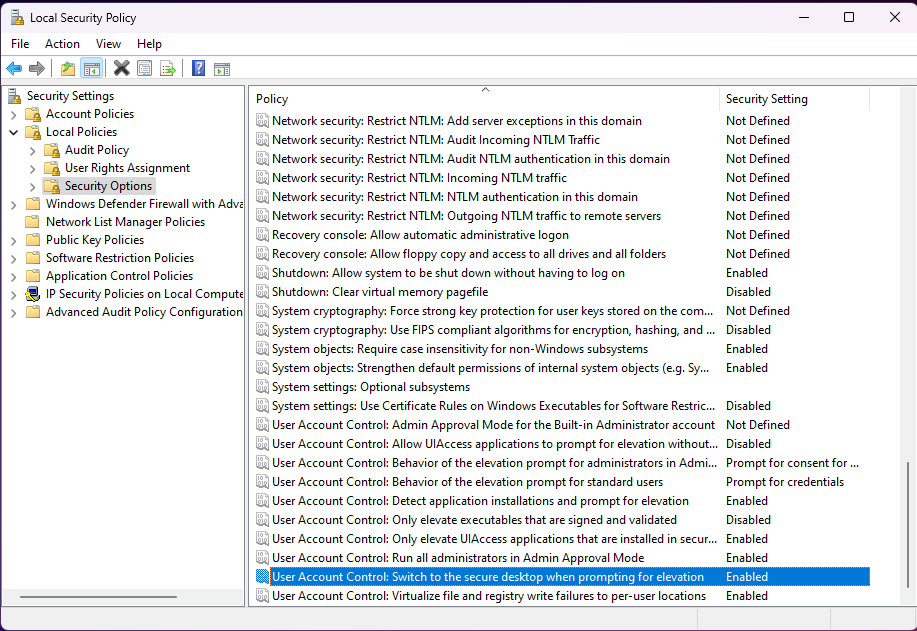
Select Disabled and click Apply.
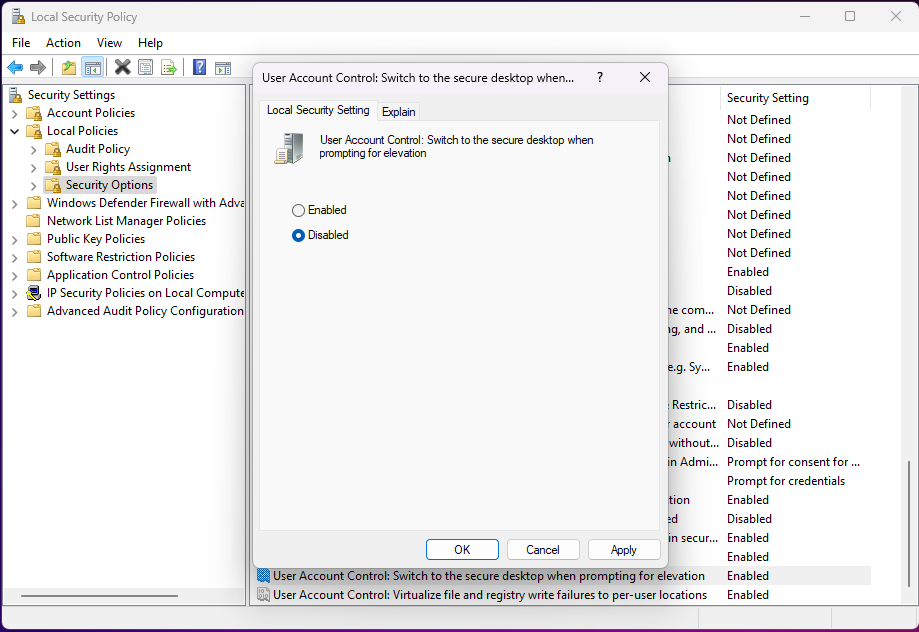
This can all be performed by the remote Quick Assist user. Now when a UAC prompt is triggered, the remote user will be able to see it and enter the necessary credentials. Be sure to re-enable the secure desktop option before you close the remote session.